On September 24, the Kharkov.News agency falsely reported that Ukrainian President Petro Poroshenko, being drunk, had been allegedly removed from a Kyiv-Moscow flight. StopFake has already explained why the news is fake.
But let’s look at the website of the Kharkov.News agency, nahnews.org. The page “About the Agency” contains the following address: Luhansk People’s Republic, Luhansk, Pochtova Street 2. It means that the website openly supports pro-Russian militants in eastern Ukraine.
It does not mean, however, that the editorial office of the website is located at the same place.
A technical description of the website could provide more information. For example, with the help of the SpyOnWeb tool, we managed to find out that nahnews.org was linked with the website of Euromaidan (emaidan.com.ua), which used the well-known, pro-Ukrainian name in order to post sometimes manipulated articles and false information.
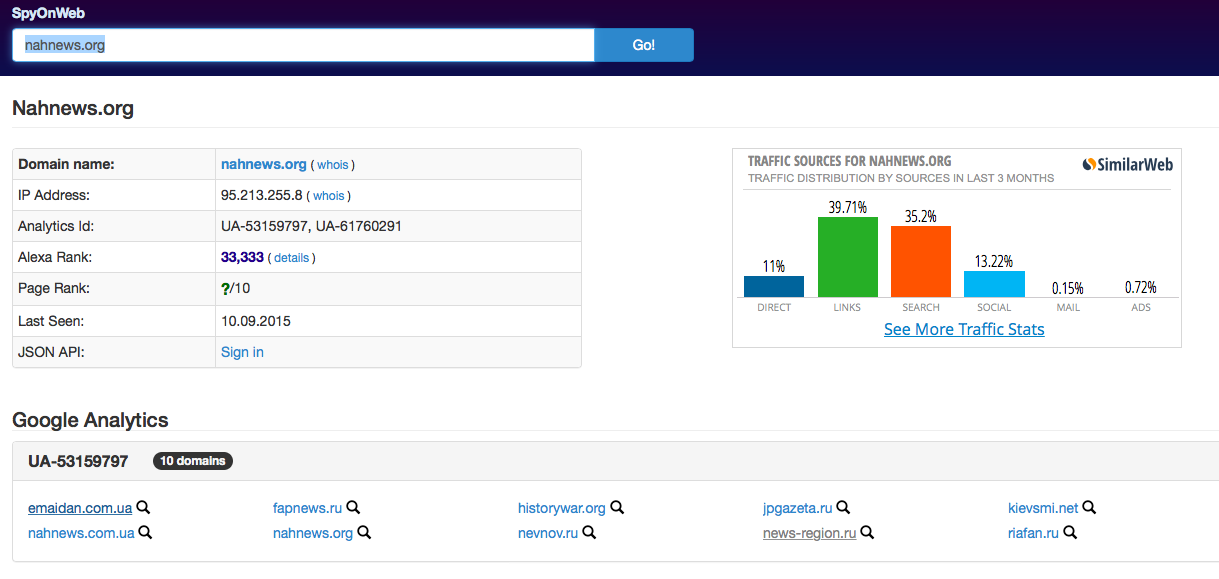
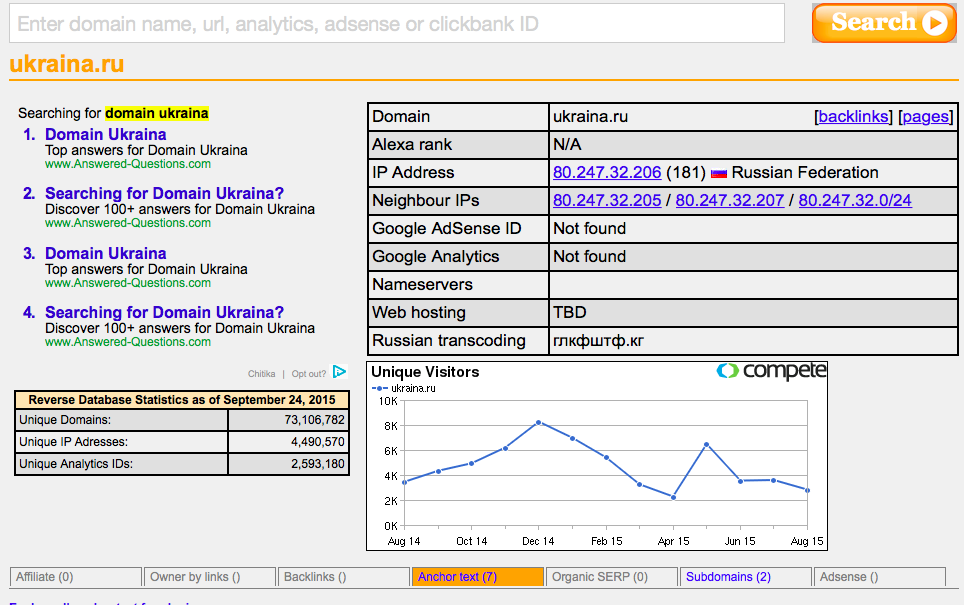
The link between these websites is also proved by the fact that they both use the same Google Analytics code. Google Analytics is a service that provides information about website traffic with the help of the special code string embedded into the html-source of a website. Every Google Analytics user gets her own unique code string and adds it to the websites that she administers. So with the help of SpyOnWeb and Google Analytics, we have found out that these two websites, as well as several news websites registered in St. Petersburg, are administered by the same person.
How to find a Google Analytics code
You can find a Google Analytics code in several ways. One of the quickest ways is to use SpyOnWeb, ReverseInternet, SameID, and Website.Informer. We recommend using all of them, as their results could differ.
For instance, SameID has a handy search for websites interconnected, not by Google Analytics codes alone, but also by the codes of AdSense, Amazon, Clickbank and Addthis that use the same principle. You could search by website domain, by code, and by IP address, which is sometimes very useful. For example, you could find an IP address among registration data and check with the help of SameID to find which other websites were registered under the same IP address. SameID allows five free search queries per day.
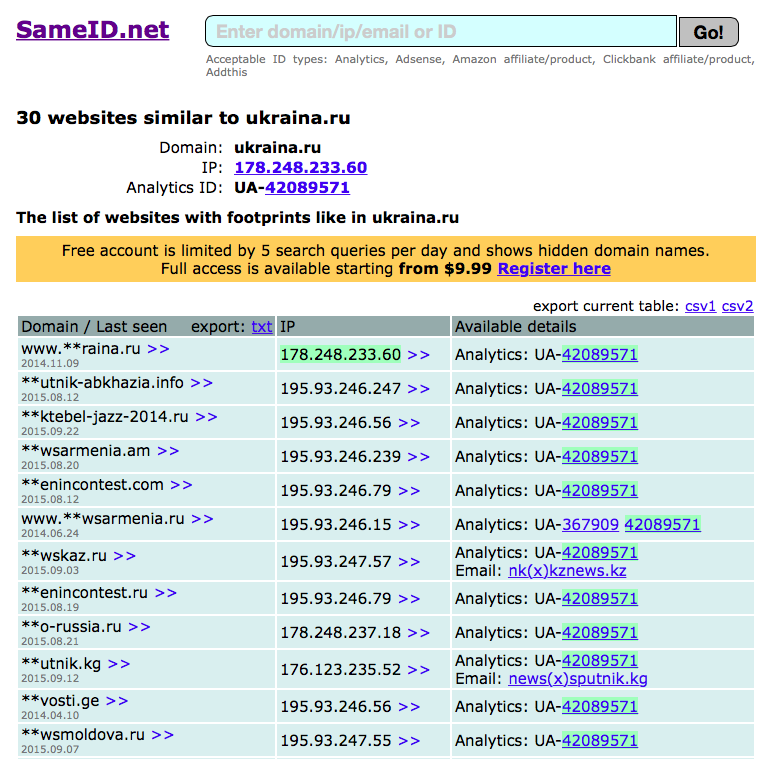
If you check the website ukraina.ru, supported by the Russia Today news agency, you will get a list of news websites from several post-Soviet countries that are administered by the same organization.
Information about domains
The Reverse Internet service provides detailed information about a domain. This tool also checks whether a Google Analytics code is available and what other sites it is linked with.
The other way to check a Google Analytics ID is to open the html-source of a page by right-clicking anywhere on the page. Then in the context menu, select “View Source” or “View Page Source” (depending on your browser).
Then you should run a search (Ctrl/cmd + F) for symbols common for all codes from Google Analytics or these other similar tools:
AdSense: Pub- / ca-pub
Google Analytics: UA-
Amazon: &tag=
AddThis: #pubid / pubid
After getting the required code you could check it in SameID or in Google.
Domain registration records and hosting
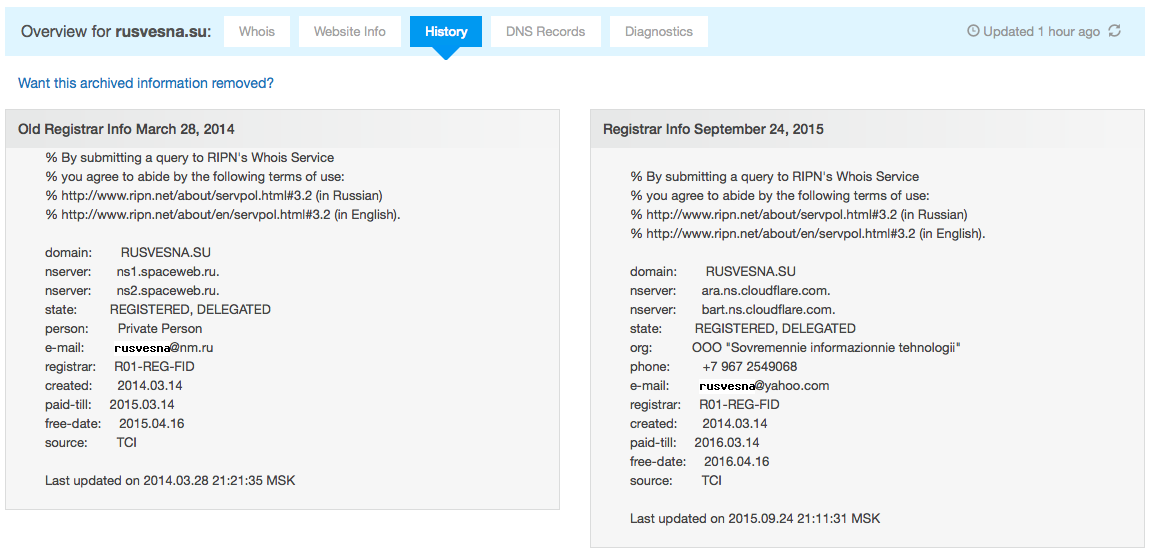
Domain registration records, available on who.is, could also be useful. Sometimes previous registration data can contain the contacts of people and organizations associated with a website.
With the help of the geoip.flagfox.net tool, you can check where a site host is (that is, its location on the Internet).

Separately, the information about a registrar, host, and Google Analytics codes could be insufficient to learn who actually administers an anonymous sites. But if you check all the linked sites one-by-one, you may find general information such as a name, an e-mail address, or an organization.
That is how Britain’s Alexander Lawrence managed to trace a network of Russian propaganda websites, administered from St. Petersburg. The identical Google Analytics code made it clear that the websites are linked. Lawrence found out the name of the administrator with the help of the e-mail address mentioned in the domain registration records. And this person turned out to be an employee of the notorious troll farm, the Internet Research Agency.
Based on materials of Bellingcat, Global Voices.
By Taras Nazaruk, for Stopfake.org.