Let’s begin with this video.
This footage became a piece of key evidence in the trial against Thomas Lubanga Dyilo. He was found guilty by the International Criminal Court of using children under the age of fifteen in the war in the Democratic Republic of Congo as soldiers and bodyguards. This video evidence was captured by a local human rights activist, Bukeni Waruzi, with the support of Witness, an international non-profit organization. Lubanga was sentenced to fourteen years of prison.
The popularity of mobile and camera devices and the growth of Internet penetration help to reveal crimes more often and in greater detail. For the last year and a half of war in eastern Ukraine, under the conditions of an information vacuum, such witness videos have been among the few sources of information about the atrocities that are happening there. For example, citizen activists and experts are trying to collect available crumbs of information about how Malaysian Airlines flight MH17 was shot down – the photo with a missile trace in the sky from July 17, 2014, and the video footage showing transportation of a BUK missile system are important resources of information. This content helps to clarify the chain of events of that tragic day.
However, is it permissible to use such footage as evidence in a court of law in order to identify and punish those responsible? The key factor in digital images is authenticity – date, time, location, and originality. Evidence could become inadmissible in a court of law if some of these factors weren’t confirmed.
For this reason, media outlets, nongovernmental organizations, and human rights activists across the world are working on implementing different types of mechanisms in order to more carefully validate the admissibility of such footage, and at the same time, to guarantee the safety of witnesses.
A few examples of such solutions have emerged in recent years. For instance, The New Yorker was among the first magazines that created a platform StrongBox to facilitate sending in material in a safe and anonymous way. With this tool anyone can send a piece of information or file to the magazine without traceable data – without email or IP addresses or data from a user’s browser or operation system. It was created on a SecureDrop project basis, which was developed by internet-activist Aaron Schwartz and is currently supported by the Freedom of the Press Foundation. The program generates a special code that is available to a person who sends information and to a magazine representative. By using this code, they can interact with each other without revealing any additional information about themselves. However, the Tor browser would be required in order to use such technology. Additionally, source anonymity excludes the possibility to verify originality of the submitted content. Today this technology is also used by other media outlets such as Forbes and The Washington Post.
In 2012, The Guardian released a smartphone application on Android called InformaCam. This application automatically collects metadata in order to identify the date, time, and location of content. While posting photos on a social network occurs with the deletion of metadata, InformaCam helps to distribute photos or videos with all available additional data such as date, time, location, nearby Wi-Fi and Bluetooth spots etc. This application also uses secure Tor software for sending information to the Guardian newsroom. This means that a smartphone user would also need to install one more application– Orbot – in order to send data safely. However, these solutions also have a range of disadvantages, making their usage less efficient.
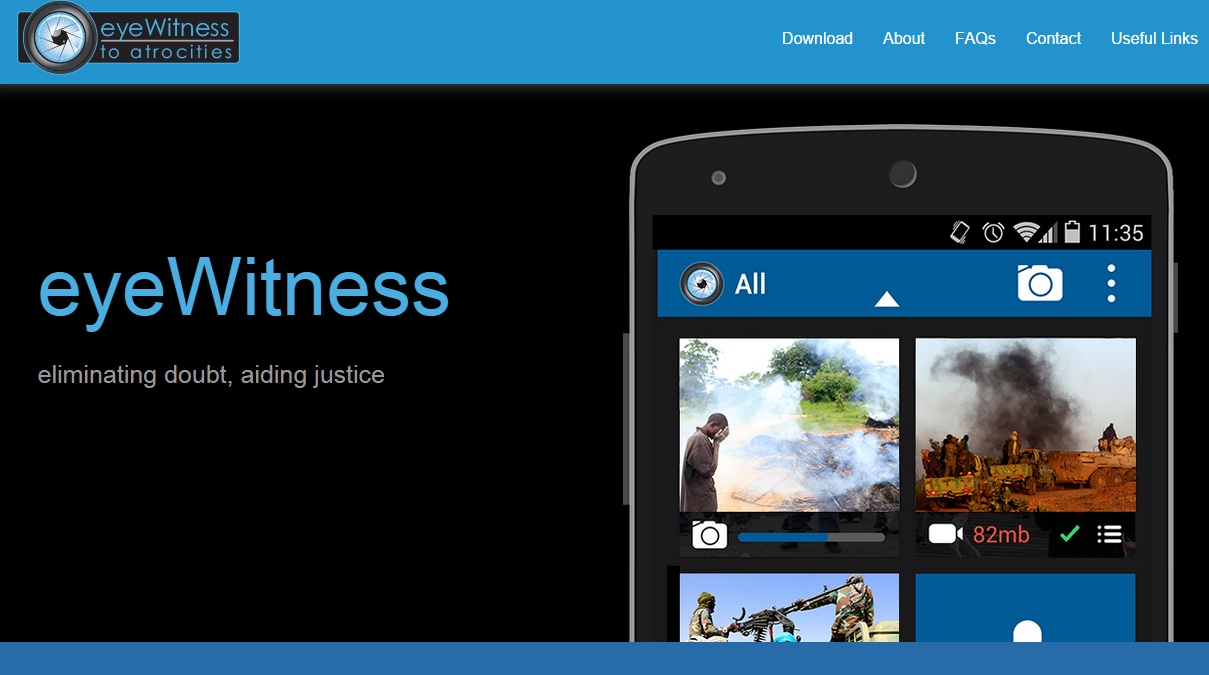
“The Eyewitness to Atrocities” tool
A few weeks ago, in order to eliminate most of the drawbacks of the other innovations, another tool for collecting witness content was launched – Eyewitness to Atrocities. This Android-based application developed in a way that helps to publish photos, footage or voice records as safely as possible and without any manipulation of the content. At the same time, there is no need to download an additional application for secure data transfers – everything is reduced to a few clicks of a button. The project was established with the support of the International Bar Association (IBA).
One of the key advantages of this application is the maximum safety of its use. The application сan only be launched by a special entry code. The footage and records made by the application are stored in a secret gallery, which is completely autonomous from the main gallery of the smartphone. Transferring content between galleries is not possible. From a smartphone, a photo or video can be sent to a secure server provided by LexisNexis, a leader in electronic database solutions. Another option is to save it on a personal memory stick.
While using the application, it is possible to stay anonymous or, if necessary, provide contact information. However, the Eyewitness doesn’t record anything off of the device, and doesn’t send any information to the external server that could identify the author of the content.
After its installation, Eyewitness shows instructions and safety tips to the user. It is also impossible to start using the application before going through the tutorial. Moreover, with a sequence of three simple steps, the application and all related content can be deleted from a smartphone.
The authors of the project also prepared a number of tutorial videos and feature reviews.
Another important advantage of the application is legal assistance in preparing footage sent by the Eyewitness to use as evidence in a court of law. For this purpose, the application was designed with legal consultations from the International Criminal Court and other tribunals. After the IBA receives content, its legal team analyzes images in terms of admissibility in a court. Then material is then sent to the proper institutions.
The main problem with digital evidence is that it is not always possible to eliminate the possibility of an image being altered from the time it is taken to the time it ends up as evidence in a court. But The Eyewitness guarantees the chain of custody and makes the manipulation of content impossible.
“Normally, the data would only be seen by our legal analysts and any appropriate international courts, such as the International Criminal Court,” says project coordinator Eleanor Farrow. This measure guarantees content authenticity, helps to identify location and time, and eliminates the possibility of editing. Additionally, before using the application, it is necessary to take six pictures in order to identify the device. Although the application is designed to work autonomously, the user has the ability to publish pictures on social networks. The available languages for the application are English, French, Arabic, Russian, and Portuguese.
However, the authenticity of content is not enough: its context plays as important role as the content itself. StopFake readers, as well as anyone who look at multiple sources in order to follow news, note how the context of a photo or video can be changed in order to misinform viewers. For instance, the so-called Slovyansk phosphor bombing video was in fact taken in Iraq in 2004. Or we recall how a photo from a film shoot was reported as an image of atrocities committed by Ukrainian troops.
The regular appearance of such cases in the media led us to ask the Eyewitness project coordinators how their team would deal with footage presenting the bombing of a residential area if its author would directly be blamed by one of the sides of the conflict for releasing such a video. Eleanor Farrow told us that the project is not able to investigate the factual accuracy of data sent via the Eyewitness: “This is because the project aims primarily to facilitate international legal proceedings, rather than to investigate the accuracy of reported events. However, the Eyewitness project does seek to support accurate media reporting. Our technology can be used to verify time, date, location, and originality.” These three factors can’t be altered while using the application.
A media outlet or other organisations can ask the IBA to provide footage sent via the application. In exceptional cases, the organisation would be ready to share this content for further investigation. Although such images normally wouldn’t be published live by the Eyewitness project, its author still has the possibility to share it on social networks. The only way to find out whether the IBA possesses any footage as evidence in an event is to send a direct request to the project representatives.
Even though atrocities are often followed by an information vacuum – or by its opposite, an information overload – sooner or later, the truth surfaces. And the technologies discussed above bring us closer to the truth.
By Taras Nazaruk, for Stopfake.org.