NEW PUBLICATION
Hybrid Analytica: Pro-Kremlin Expert Propaganda in Moscow, Europe and the U.S.: A Case Study on Think Tanks and Universities
The Institute of Modern Russia (IMR) has published a new report by Dr. Kateryna Smagliy, with contributions by Ilya Zaslavskiy, that traces the insidious web of connections between Russian oligarchs and Western research institutions. Dr. Smagliy was a Special Fellow at the European Values Think-Tank during the summer of 2018.
The report examines the Kremlin’s connections with think tanks, universities, and research institutions in Russia, Europe, and the United States, including its co-optation of Russian and Western experts into the pool of proxy communicators for the Putin regime. The report argues that Western governments and academic institutions should acknowledge the threat posed by Russia’s information warfare, step up efforts to expose the Kremlin’s network of agents within Western academia, and adopt mechanisms to safeguard professional integrity and due diligence processes.
The Prague Manual: How to Counter the Kremlin’s Influence in Europe
Germany’s Federal Academy for Security Policy has published a summary of our milestone Kremlin Watch report, The Prague Manual, as a Security Policy Working Paper, listing eight priority steps for EU member states based on their threat awareness of the Kremlin’s influence.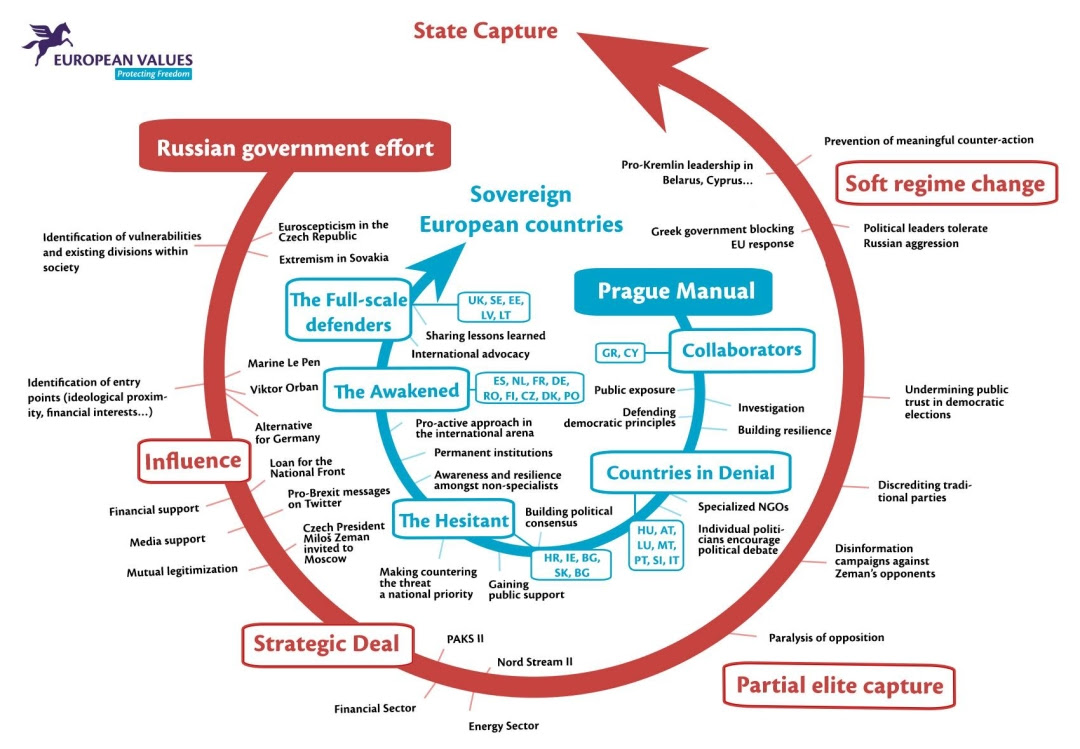
Don’t forget to visit our website, where you can find all previous Kremlin Watch reports, as well as an interactive map with countermeasures designed and implemented by EU Member States.
ANNOUNCEMENT
Jakub Kalenský, the Czech Republic’s seconded national expert at the EEAS East Stratcom Task Force, will be ending his tenure with the Task Force this month. Thanks to his tenacity and passion, as well as those of his fellow team members, the Task Force has evolved into the preeminent international authority on Russian disinformation, despite facing many challenges, controversy, and (of course) the unrelenting delight of troll attacks.
The Kremlin Watch team offers Jakub sincere congratulations and well wishes for his next chapter.
Topics of the Week
Bellingcat has revealed that the second Skripal suspect – alias Alexander Petrov – is in fact Dr. Alexander Mishkin, a military doctor employed by the GRU.
The Dutch government has revealed details of a counterintelligence operation that led to the arrest of four GRU agents attempting to hack the OPCW, a chemical weapons watchdog investigating the use of Novichok in Salisbury.
The US Justice Department has indicted seven GRU operatives for executing a “persistent and sophisticated” cyber campaign against US and international anti-doping agencies, amongst other targets.
An explosive investigation alleges how Chinese spies have been embedding virtually undetectable microchips into hardware used by US government agencies and companies, enabling remote infiltration of computers and networks.
Special Focus: The Russian Orthodox Church is pulling out all the stops to thwart the Ukrainian Orthodox Church autocephaly project.
Good Old Soviet Joke
An American is traveling through the Soviet Union. While on a train heading to Leningrad, listening to his handheld radio, he is interrupted by another passenger.
“You know, we make those better and more efficiently here in the Soviet Union,” the passenger says.
“Is that right?” the American asks.
“Yes,” the passenger replies confidently. “What is it?”
Policy & Research News
Bellingcat identifies second Skripal suspect
On Monday, Bellingcat revealed the identity of the second suspect in the Skripal poisoning case. The news comes just two weeks after Bellingcat published a landmark investigation conclusively establishing the identity of the first suspect (alias Ruslan Boshirov) as GRU Colonel Anatoliy Chepiga, recipient of Russia’s highest state honour.
Bellingcat investigators report that Chepiga’s co-conspirator, who travelled to Salisbury under the alias Alexander Petrov, is in fact Dr. Alexander Yevgenyevich Mishkin, a trained military doctor employed by the GRU. A detailed identification process that included multiple open sources, testimony from individuals familiar with Mishkin, and copies of identifying documents provides key information about Mishkin’s background: born in 1979, Mishkin graduated from an elite Russian Military Medical Academy and was recruited by the GRU during his studies. In 2010, he relocated to Moscow, where he received his undercover identity and the alias Alexander Petrov. Mishkin’s current military rank is unknown, but it is likely that at the time of the Skripal poisoning, he was either a Lt. Colonel or a full Colonel. Bellingcat’s full report of the investigation and identification process will be published on Oct. 9.
Is Russian intelligence losing its touch? GRU blunder in the Netherlands
Last week saw yet another major spy story featuring the GRU. The Dutch government revealed details of a counter-intelligence operation from last April in which four GRU agents were caught attempting to hack the OPCW – the chemical weapons watchdog investigating the use of Novichok in Salisbury and the alleged gas attack in Douma by the Syrian regime.
The Financial Times provides a breakdown of how the counter-intelligence operation unfolded and how the GRU agents were caught with hacking equipment near the OPCW headquarters. Dutch intelligence authorities seized the equipment and placed the GRU operatives on a plane back to Russia. The decision to expel the agents rather than arrest them raised a number of questions. The Dutch Prime Minister justified the move on grounds that the matter was an intelligence operation and not a criminal inquiry.
Using the press release and information provided by the Dutch intelligence services, Bellingcat and The Insider managed to trace the car registration of an identified GRU agent to the address of GRU Unit 26165, which is known as the GRU’s cyberoperations centre. In the process, they also identified a total of 305 individuals – along with their names, birthdates, and phone numbers – whose cars were registered to the same address. If these 305 individuals are indeed affiliated with Unit 26165, the leaking of their identities constitutes one of the largest breaches of personal data of a state intelligence service. As to why the intelligence officers might list car registrations on an accessible database, Alex Gabuev explains that registering a car to the GRU’s address would offer benefits such as exemptions from car tax, traffic police, fines, and more.
New study on the spread of misinformation in the 2016 presidential election
A recent study by the Knight Foundation, which analyses over 10 million tweets from 700,000 Twitter accounts that linked to more than 600 misinformation or conspiracy news outlets, concludes that the concentrated ‘fake news’ ecosystem which was active during the 2016 election has continued operating to this day.
The study finds that over 80% of the accounts that repeatedly spread misinformation during the 2016 election are still active today, jointly publishing more than one million tweets a day. Of these tweets, over 65% contain links to misinformation that originates on just 10 websites. The study also reveals that while the majority of misinformation was related to Republican and pro-Trump accounts during the 2016 election, a substantial share of misinformation was also spread by Democratic-identified accounts disseminating anti-Clinton related misinformation from Russian propaganda outlets such as RT and Sputnik.
Why we’re still catching up and losing against fake news
An article on the fight between regulators and spread of disinformation argues that regulators are still stuck in 2016 when it comes to addressing fake news and online disinformation, failing to account for new forms and methods of spreading deceptive content. Since 2016, the means of producing and disseminating disinformation and fake news have become increasingly sophisticated – from poorly-written social media posts to carefully crafted images and video that are in the grey area of ‘fake news’ and political satire. Additionally, disinformation campaigns have infiltrated other platforms such as WhatsApp, whose encryption makes it much harder to tackle disinformation effectively.
The European Commission’s disinformation ‘code of practice’ is to be unveiled later this month, but due to the aforementioned challenges and scope of the problem, it is likely to fall short of effectively countering disinformation on social media.
US Developments
Russian operatives charged over global hacking campaign
Following the July indictment of 12 Russian military intelligence officers, Justice Department officials have leveled criminal charges against another seven Russian GRU operatives, currently outside the reach of US jurisdiction. The Russian entourage is accused of conducting a “persistent and sophisticated” cyber campaign against US and international anti-doping agencies that had previously exposed an extensive Kremlin-sponsored doping program, resulting in the banning of Russian athletes from several international events, including the Olympics. “In many instances, the stolen information was publicized by the GRU as part of a related ‘influence and disinformation’ campaign designed to undermine the legitimate interests of the victims, further Russian interests, retaliate against Russia’s detractors and sway public opinion in Russia’s favor”, the indictment alleges.
Among the other targets of the four-year hacking campaign were the foiled cyber intrusions against the Netherlands-based OPCW (see above) and a US nuclear energy company, Westinghouse Electric Company, where employees had been involved in “advanced nuclear reactor development and new reactor technology”.
Russia’s disinformation machine goes into overdrive
Shortly after US, British, and Dutch officials condemned Russia for its involvement in the aforementioned series of cyber-attacks, Russia’s Ministry of Defense issued its own extraordinary accusations against the US. In a poorly-disguised attempt to deflect Western attention, curiously timed ‘revelations’ assert that the US has been operating a clandestine biological weapons program in Georgia, posing as a public health facility, which supposedly led to 73 deaths in clinical trials. A Pentagon spokesman swiftly dismissed the claims as “an invention of the imaginative and false Russian disinformation campaign against the West” and labeled them “obvious attempts to divert attention from Russia’s bad behavior on many fronts”.
Ironically, the audaciously false allegations, which further bemoaned the US for “flouting international agreements”, also trail international scrutiny over Moscow’s apparent violation of a key Cold War arms control treaty. Prior to the statements made by Russia’s Defense Ministry, both NATO and the US had taken Moscow to task for what is believed to be a contravention of the 1987 Intermediate Range Nuclear Forces treaty, which prohibits a class of missiles that could be used to strike the European continent.
“The Big Hack”: Chinese spies claim to have infiltrated 30 US companies
Chinese operatives have been embedding tiny, near undetectable microchips into hardware used by multiple US government agencies and companies that enable remote infiltration of computers and networks. Citing 17 anonymous sources, Bloomberg reports that Chinese spies installed hardware exploits – chips as small as the tip of a sharpened pencil – within motherboards whilst on production lines in China, as part of an unprecedented and thoroughly surreptitious supply chain attack. Indeed, according to a Pentagon report released shortly after, China’s near monopoly on the world’s technology supply chain, which by some estimates manufactures 70% of the world’s mobile phones and 90% of its computers, presents a “significant and growing risk to the supply of materials and technologies deemed strategic and critical to US national security”.
However, among the approximately 30 companies affected, Amazon, Apple and Supermicro (the latter of which claimed to be responsible for supplying infected hardware) have challenged the veracity of Bloomberg’s explosive report. Whether or not this attack is ultimately verified by an official investigation, given the previous moves against Chinese tech firms, the plausibility alone renders Beijing open to significant political and economic repercussions.
SPECIAL FOCUS
Impending Ukrainian Orthodox autocephaly: A major blow for Russia
With the Ukrainian Orthodox Church’s autocephaly project approaching a finale in the upcoming week, the Russian Orthodox Church has continued working overtime to exhaust all possible routes to undermine the effort.
Realizing that the Ecumenical Patriarchate – which is responsible for overseeing the autocephaly project – remains unresponsive to the criticisms of the Russian Orthodox Church, the latter has instigated a policy of coercing as many other Orthodox Christian jurisdictions as possible to call for a postponement of the long-awaited independenceand a series of councils to discuss the issue. Knowing full well that such events take a significant amount of time to organize, the Russian Orthodox Church is utilizing this strategy in hopes of indefinitely postponing the autocephaly.
In addition, the Moscow Patriarchate has been notably effective at manipulating media and public perception of the issue. For instance, it recently reported that the Estonian Orthodox Church condemned the Ecumenical Patriarchate’s “interference in Ukraine”; however, it failed to specify that it was the Estonian Orthodox Church-Moscow Patriarchate (a proxy of the Russian Church) that gave this statement, and not the Estonian Apostolic Orthodox Church itself, which has national pre-eminence and falls under the Ecumenical Patriarchate. Such tactics are intended to give the illusion that all Orthodox jurisdictions support the activities of the Moscow Patriarchate and oppose autocephaly for the Ukrainian Orthodox Church.
The Russian Orthodox Church’s promotion of the Kremlin’s geopolitical agenda is a well-established fact, and it is thus unsurprising that the Church would aim to block the autocephaly project and instead promote the concept of Russkiy Mir. Careful monitoring of these developments is paramount, especially as Russia’s potential reprisals against Ukraine remain uncertain.
The Kremlin’s Current Narrative
Playing the victim: The Kremlin’s temper tantrum
Given Russia’s unrelenting espionage and disinformation efforts, European and Western nations have been pressed to develop a wider range of capabilities to defend themselves and effectively counter the increasingly assertive Putin regime. To this end, British defense officials recently announced that they have been practicing cybersecurity initiatives that could for instance remotely manipulate electricity in Moscow should Russian belligerence increase.
As expected, Russian state-media outlets were quick to provide their own interpretation of the announcement, sensationalizing headlines to imply that Britain is on the verge of directing a cyberattack against Russia. In addition, Russian media ridiculed Britain for having to resort to such tactics due to being unable to engage in physical warfare against Russia. Apparently, Britain being one of NATO’s founding members is an irrelevant fact. And in the ultimate irony, Russian state media also reported how members of the Federal Assembly of Russia criticized the British cybersecurity initiative as “unbefitting a civilized government”. (Yes, you read that right.)
It should go without saying how laughable such statements, taken in context of the Kremlin’s relentless pursuit of propaganda, cyberterrorism, and political interference vis-à-vis Western nations. This news coverage only betrays the Kremlin’s continuous desire to instil fear, confusion, and doubt within the European public (as well as the domestic Russian population, to ensure passivity), and to warp perceptions of reality in its own favour, projecting itself not as the aggressor but rather the innocent and unfairly maligned victim of sanctions, NATO enlargement, and other forms of Western ‘hostility’ and ‘aggression’.
Kremlin Watch Reading Suggestion
Russian Use of Private Military and Security Companies:
The Implications for European and Norwegian Security
The Norwegian Defence Research Establishment has published a report analysing the nature of Russian private military and security companies (PMSCs) and contrasting it to that of their Western counterparts. In the West, the PMSC industry is heterogeneous and serves to carry out support, fill gaps in military organisation, and equip operations. Services provided by Western PMSCs can be categorized as protective security services, military support, and state building services. In 2003, the Western PMSC industry drew a lot of negative attention for its conduct in Iraq. As a consequence, many companies shied away from a military profile and rebranded themselves as ‘risk management companies’ or ‘risk consultancies’.
Although not officially legal, the Russian PMSC industry does not feel a need to disassociate itself from a military profile and tends to deliver combat services. For example, RSB-Group has been engaged in the protection of naval vessels in African waters, mine clearance in Libya, and was allegedly part of the annexation of Crimea in 2014. Interestingly, the RSB-Group was the first Russian PMSC to open a cyber defence detachment in 2016. Russian PMSCs that have been reported to be involved in Donbass include the RSB-Group, MAR, ENOT Corp, and Wagner.
The report offers five potential consequences for the international community to consider:
- Russian PMSCs may have a particularly low threshold for endangering civilian lives;
- They may be more willing to serve customers with questionable human rights records;
- Russian PMSCs may be hired to augment the capacity of actors that European militaries fight against;
- They may be fighting on behalf of the Russian government in conflicts outside Europe where European militaries are also involved;
- Actors that are the allies of European countries in non-European conflicts may still hire Russian PMSCs to boost their military capacities.
Kremlin Watch is a strategic program of the European Values Think-Tank, which aims to expose and confront instruments of Russian influence and disinformation operations focused against liberal-democratic system.