By Nika Aleksejeva, with Roman Osadchuk, Sopo Gelava, Jean Le Roux, Mattia Caniglia, Daniel Suárez Pérez, and Alyssa Kann, for DFRLab
Network uncovered by the DFRLab promoted Kremlin narratives in Germany, France, Italy, Ukraine, Latvia and the UK
In August 2022, the DFRLab independently discovered a small network consisting of six inauthentic Facebook pages purchasing ads to promote posts about Germany’s impending energy crisis and called for the lifting of sanctions on Russian gas imports. A review of these assets by Meta, along with others separately identified by German media, led to the discovery of a much larger network consisting of 1,633 accounts, 703 pages, twenty-nine Instagram profiles, and one Facebook group. These assets promoted Kremlin interests beyond Germany, also targeting France, the UK, Italy, Ukraine, and Latvia.
The network exhibited an overarching pattern of targeting Europe with anti-Ukraine narratives and expressions of support for Russian interests. It manifested multiple indicators of previous Russian influence operations, including those conducted by the Kremlin itself and those whose operators remain unknown but align with Kremlin interests in the region and around the world. This includes the amplification of pro-Kremlin and anti-Ukraine or anti-Western narratives; the paid promotion of content; calls for action on petition sites and other forms of audience engagement; amplification across multiple languages reflecting inaccurate and non-native grammar; impersonating real people or institutions or creating fake ones; and generating names with detectable patterns.
Meta concluded that the network originated in Russia, and spread out across multiple platforms beyond Facebook and Instagram. According to a spokesperson from Meta:
We took down a large network that originated in Russia and targeted primarily Germany, and also France, Italy, Ukraine and the United Kingdom. The operation began in May of this year and centered around a sprawling network of over sixty websites carefully impersonating legitimate news organizations in Europe, including Spiegel, The Guardian, Bild and ANSA. There, they would post original articles that criticized Ukraine and Ukrainian refugees, praised Russia, and argued that Western sanctions on Russia would backfire. They would then promote these articles and also original memes and YouTube videos across many internet services, including Facebook, Instagram, Telegram, Twitter, petitions websites Change.org and Avaaz.com, and even LiveJournal.
Meta noted that approximately 4,000 accounts followed one or more of the Facebook pages within the network, while around 1,500 accounts followed one or more of the Instagram accounts. The network spent the equivalent of about $105,000 in advertising on Facebook and Instagram, primarily in US dollars and euros; the DFRLab also identified advertisements purchased with Hungarian forints.
Meta also added that the majority of the accounts, pages and ads were detected and removed by its automated systems. Because of this, the DFRLab was unable to review the entire network, but still managed to analyze nearly 1,000 of the 2,366 total assets involved.
As noted by Meta, some of the Facebook pages within the network posted links to websites of Russian origin, as well as links spoofing the domains of legitimate media organizations, including Bild and Welt in Germany, 20minutes in France, ANSA in Italy, RBC in Ukraine, and the Guardian in the UK. In some cases, the network used advertisements to promote posts primarily to German, French and Italian audiences.
The Russian network targeted Germany and Latvia with narratives about impending hardships resulting from sanctions targeting Russian energy supplies. In France and Italy, the network targeted Facebook users with posts that called for an end to weapons shipments to Ukraine. The timing and narratives of the posts coincided with policy decisions made by the targeted countries pages regarding the war in Ukraine. For example, German Chancellor Olaf Scholz went to Canada for talks about liquified natural gas supplies on August 21, 2022. On August 22 and 23, five pages in the network posted a cartoon portraying Europe as a character named “Dr. EuroReich,” who is seen cutting Russian gas to a patient representing Germany’s economy. Similarly, in June 2022, France completed its first delivery of Caesar self-propelled howitzers to Ukraine. At the end of that month, four pages posted an image of the howitzer and suggested that France was getting itself involved in war crimes allegedly committed by Ukraine.
Additionally, some of user accounts within the network used AI-generated profile images or images of real people retrieved from the web.
Discovering the inauthentic network
The DFRLab first identified the network beginning with Facebook page called Winsome wc5. The sole post on its page called for the implementation of the Nord Stream 2 gas pipeline, which would deliver Russian gas to Germany. The post, which was promoted by five Facebook ads, garnered 305 reactions, 39 comments, and 65 shares.

The Winsome wc5 Facebook page categorized itself as a restaurant and used the logo of popular German media outlet Frankfurter Allgemeine Zeitung (FAZ) for its profile image, likely to create a veneer of credibility.

The sole post from Winsome wc5 called on Facebook users to click on a link that led to the subdomain news.bild.llc. This is likely intended to trick users into thinking that the page was associated with Bild, a popular German tabloid. The page led to a plain-text story about an old dog. The passage was taken from a German fairy tale published by the Brothers Grimm.
The DFRLab located five other Facebook pages that posted links to the news.bild.llc subdomain. The posts claimed that the majority of Germans were against sanctions targeting Russia, warned of the danger posed by a nuclear power, criticized the idea of using electricity to heat houses, and promoted a small demonstration alleging that the Ukrainian Armed Forces were “killing children” in the Donbas region. Five out of the six pages purchased Facebook ads to promote their posts.

The network
Facebook identified 703 pages that belonged to the network, 169 of which were reviewed by the DFRLab. The pages were created between April 2022 and August 2022, with most pages created on two dates: June 29, 2022 and July 2, 2022.
The naming conventions for these pages followed five general patterns:
· Positive-sounding adjectives in combination with two letters and one number (eighty-one pages)
· The phrase “open opinion” in various languages (six German pages, fourteen French pages, six Italian pages, and two Latvian pages)
· Names of people (nineteen pages)
· Imitating a media outlet (ten German pages and one US page)
· The Ukrainian phrase “Вільний народ” (“Free Nation”) (four pages)
The remaining twenty-six pages did not form any separate category and were categorized as “other.”
https://flo.uri.sh/visualisation/11243942/embedA circle hierarchy chart showing naming pattern (general circles), page manager location (first degree inner circles), and language group that page targeted with their identities (inner circles). (Source: @nikaaleksejeva/DFRLab via Facebook)
Eighty-one pages in the set used a name pattern that consisted of positive adjective, two letters, and one number. In thirty-nine of these cases, the location of the page managers was listed as Ukraine. The managers’ locations of the rest were unknown. Forty pages had posted at least once, including eleven posts in German. Twenty-nine posts featured food recipes in Russian.

For most of the pages utilizing the name “Open Opinion” in multiple languages, the location of the manager was unlisted, though six of them listed Ukraine. Three of these pages targeted Germany with their posts.

There were also pages named after people, some of which appeared to employ AI-generated or stolen images as their profile pictures. One page listed its administrator’s location as Belarus, while another listed Ukraine. The rest of them did not feature a location.

A recurring feature among many pages across these three categories was the repeated use of Frankfurter Allgemeine Zeitung’s logo as their profile images. In total, sixty-four pages utilized the FAZ logo. Eleven additional pages used the names of other popular German media outlets, including Junge Welt, Welt, and Westdeutsche Allgemeine Zeitung (WAZ). One page impersonated US broadcaster ABC News.


A small cluster four pages used the Ukrainian name Вільний народ (“Free Nation”), displaying a Ukrainian flag as their profile images. Another page named “Diana Hertisson” also displayed the Ukrainian flag as its profile image.
The content
Out of the 169 Facebook pages reviewed by the DFRLab, 122 of them had not posted any content. Among the remaining forty-seven pages, only three of them posted extensively, usually linking to legitimate media outlets. Forty-four pages, on the other hand, featured one to four posts each blaming Ukraine for hardships facing Europe and Russia.
Many of these anti-Ukraine posts repeated across other pages. For instance, a cartoon showing a character called “Dr. EuroReich” cutting Russian gas to Germany appeared on six pages. Five of these posts appeared on August 22 and August 23 but garnered no engagement. The sixth post, published on August 26, garnered 377 reactions, 77 comments and 91 shares.

Notably, the Russian embassy in France tweeted a similar hand-drawn cartoon featuring “Dr. EuroReich” in March 2022, then quickly deleted it.
https://cdn.embedly.com/widgets/media.html?type=text%2Fhtml&key=a19fcc184b9711e1b4764040d3dc5c07&schema=twitter&url=https%3A//twitter.com/AricToler/status/1507026032011972611&image=A previous version of the Dr. EuroReich character, tweeted and deleted by @AmbRusFrance in March 2022, which was preserved by Aric Toler of Bellingcat. (Source: @AricToler/archive)
Another set of duplicate posts called on Europe to stop supplying Ukraine with weapons. Three pages named “Lowe Guzman,” “Gilmore Stanton,” and “Estes Pineda” shared link to a petition on Change.org. The posts appeared July 9–12, 2022. The posts by Gilmore Stanton and Estes Pineda were in French, while Lowe Guzman posted in grammatically incorrect Italian. Estes Pineda’s post in French garnered minor engagement (23 reactions and 5 comments), while Lowe Guzman’s post in Italian garnered 384 reactions, 215 comments, and 23 shares.

Incorrect grammar is a common indicator in Russian influence operations previously identified by the DFRLab. In this particular example, the Italian example included the phrase “Smettila di inviare armi in Ucraina!” (“Stop sending weapons to Ukraine!”) The correct form should have been something along the lines of “Basta all’invio di armi all’Ucraina” or “Stop all’invio di armi all’Ucraina.” This tells us that probably the person writing it used an online translator or does not have a deep knowledge of Italian. It is also noteworthy that they decided to target Italy with this messaging, as sending weapons to Ukraine is unpopular and a political aim of far-right parties such as Lega Nord and the 5 Stars Movement. Prior to the ad being promoted, the Draghi government battled to get its weapons support package approved by the Italian parliament. According to a poll conducted at that time by Rai1 TV, 45 percent of Italians were against sending weapons to Ukraine.
Meanwhile, four pages within the network promoted a Facebook Story with an accompanying text implying that France is committing war crimes by sending weapons to Ukraine. Three pages were named Opinion ouverte in French, while one in Italian was named Opinione aperta, both of which translate to “open opinion” in English. (A similarly named page in German, Offne Meinung, shared the aforementioned “Dr. EuroReich” cartoon.) The French and Italian pages published posted similar posts between June 26–30, 2022, garnering limited engagement.

The above examples illustrate the most common narrative themes seen across pages in the network. Namely, sixteen posts represented the theme that the economy is getting worse due to Russian sanctions, with eleven of these posts targeting Germany. Fifteen posts targeting France and Italy focused on the narrative that Europe should stop supplying Ukraine with weapons. Italian-language pages also spread the narrative that Ukraine was leading the world into a food crisis, while three posts in German and French demanded that Europe should not cancel Russian culture. Additional narratives involved Germany being overwhelmed by Ukrainian refugees and Poland allegedly wanting to annex part of Ukraine, among others.

Paid promotion of the posts
The DFRLab identified thirteen pages that spent money on Facebook ads, five of which were still accessible in Meta’s Ad Library at the time of our research. Six ads targeted Germany. There were three pages that advertised the same post alleging that “Germans were brought onto the streets” to protest “the war against Russia.” The promoted posts included a link leading to the domain news.welt.ltd, similar to the domain news.bild.ltd discovered during initial DFRLab research; Welt is another popular media outlet in Germany.

One of the three other posts targeting Germany was about “children being killed” by Ukrainians in eastern Ukraine. It promoted the URL truemaps.info, which leads to a map of the world where North America, the European Union and Australia are marked as responsible for “killing children in Donbas, Ukraine.” Meta ultimately removed the post. Another post was about Nazi symbols used by Azov Battalion fighters in Ukraine. The Azov Battalion ad was the most expensive reviewed by the DFRLab; according to the Ad Library, it cost as much as $2,000, garnering between 500,000 and 600,000 impressions.


Similarly, France was targeted by five ads within the network. Three pages all named Opinion ouverte promoted posts suggesting that Ukraine is likely to lead the world into a food crisis. The most expensive ad cost more than €700; it was taken down by Meta.

The other two ads targeting France were also taken down by Meta. One of them promoted truemaps.info, while another accused European Commission President Ursula von der Leyen of nepotism and linked to an article on 20minuts.com, a spoofed version of legitimate French media outlet 20minutes.fr.

The DFRLab could identify only one ad targeting Italy. It led to an article titled “Poland stopping aid for Ukrainian refugees,” with accompanying text that asked, “When will they start working and providing for themselves?” Curiously, the ad was paid for in Hungarian forints. Another ad — a video calling on people not to “cancel Russian culture” — targeted Facebook and Instagram users in the UK.

Inauthentic users
Facebook identified 1,633 user accounts within the network, of which the DFRLab reviewed approximately 300, as the rest had already been de-platformed. Accounts featured both names in Cyrillic and Latin letters. Most of the assets were empty or had their accounts protected, meaning that nothing outside of changes to profile and cover pictures was available. Some accounts featured multiple profile picture changes within a day, portraying different people, including AI-generated faces. While these faces did not repeat across account profile pictures, the DFRLab identified that same cover photos across multiple accounts. Moreover, some names and profile pictures did not match in terms of gender, usually featuring male names and female profile pictures.

The DFRLab identified multiple accounts that stole images from VKontakte users. Below is an example of an account with a male name and a stolen VK photo of a Kazakh woman.

Accounts also showcased several profile pictures that appear to be AI-generated. The DFRLab established this by comparing the consistent positioning of the eyes no matter the facial type.

Accounts also seemed to simulate real users by inserting information in their “About” sections. For instance, several accounts assigned random interests like “traveling” or “cooking,” while also listing where they were from, where they currently lived, their place of work, and educational background. However, a lack of care was evident in how the fields were filled. The network’s operators tried to match a user’s hometown and current location with their places of work and study, which in some cases led to odd results that either suggested automation or zero knowledge of the region and the Ukrainian language. For instance, the account “Алёна Бельдинова” (Alyona Beldinova) indicated that she’s from Fastiv and works at Fastiv Region News, a fringe aggregator of Kyiv regional news. The account stated that she studied at Manicure Fastiv, which is probably a random entry in the list of pages under the search term ‘Fastiv.’ Another account studied at “Territorial defense forces” and listed that phrase as its location as well.
Finally, one account revealed a possible Russian origin when it mentioned that they studied at and worked at the Municipal guard at Vasylkiv, Ukraine, yet lived in Wasilków, Poland. In Russian, both cities are pronounced and spelled “Vasil’kov” (“Васильков”). It is likely that when creating the account, the network entered the Russian spelling of the city and accidentally populated it with Wasilków, Poland instead.

The network also comprised forty-seven Instagram accounts, twenty-eight of which were down at the time of our research. Seventeen of the live accounts had empty timelines, with the number of followers or the accounts they followed close to zero. At least five of these accounts had stolen profile pictures from elsewhere on the internet and were likely inauthentic.

The usernames of sixteen accounts were likely automatically generated based on a familiar pattern: the word “opinion” followed random numbers; others utilized ouverte, the French word for “open.” As noted earlier, Facebook pages within this network also used forms of the words “open” and “opinion” in their names. Similarly, three accounts’ usernames mimicked names of German media outlets, such as Welt and Junger Welt. In addition, a majority of the Instagram accounts reviewed by the DFRLab contained German usernames, suggesting that the Instagram assets targeted German-speaking audiences.

Seeking attribution
The DFRLab examined domains that were amplified by the network via Facebook ads. For example, a page named “Comely ds4” directed users to a Telegram post that linked to an article on anachrichten.de.

Forensic analysis of the Anachrichten.de domain revealed that it was hosted in St. Petersburg. Some of the images on the website were hosted on Ana-de.net with Russian file names, like “Снимок экрана” (“screenshot”). The Anachrichten article that used images hosted on Ana-de.net was authored by Vitaly Volkov, who has worked as the lead analyst of a Russian foundation named Eurasia Heritage since 2021.

Additionally, Ana-de.net shares the same registration email, [email protected], as Crimea-land.com. It is unclear what the first half of the email, “sib,” refers to, but “kulak” means “fist” in Russian. The names of the registrants for both domains are Russian-sounding, and likely inauthentic.

Other Facebook pages also pushed ads leading to previously mentioned spoofed domains like welt.ltd, 20minuts.com, and ansa.ltd.

Each of these websites spoofed a mainstream media outlet: Welt.ltd imitated Germany’s Welt.de; 20minuts.com imitated France’s 20minutes.fr; and ANSA.ltd spoofed Italy’s ANSA.it. The websites were cloned in such a way that clicking on any of the links on the fabricated website would redirect the user back to the original website, creating a cloak of legitimacy.
For example, an article published on Welt.de on July 27, 2022, was cloned onto Welt.ltd. Evidence of this can be found in both the source code and URL, which referenced the original article number (2401282777) on the cloned website.
The cloned article was subsequently distributed by the network uncovered by the DFRLab.

Another commonality shared by these websites is that they were eventually aggregated to RRNews.world, using the same text and banner images.
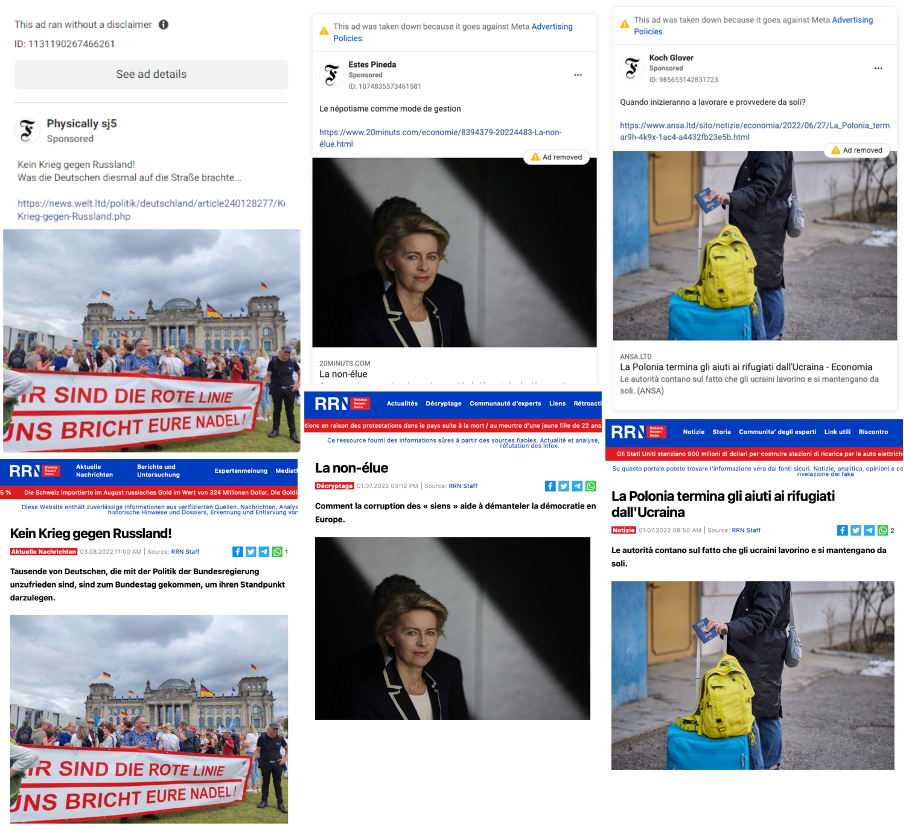
The DFRLab identified eight Facebook pages within the network that linked to RRN.world.

Although RRN.world presents itself as “Reliable Recent News,” the DFRLab has identified links to Russia that go beyond amplifying pro-Kremlin articles. Until early June 2022, the site used the domain “RRussianNews.com,” a nod to its pro-Russian content. Although the current domain uses a privacy proxy to hide the details of the domain registrant, RRussianews.com didn’t take such precautions. As a result, the DFRLab identified a Russian phone number and Yandex email address that were used to register the domain in March 2022.

Today, RRussianews.com redirects to RRN.world.

Conclusion
This inauthentic network of more than 2,300 assets across Facebook and Instagram. These included pages identified by the DFRLab which directed their readers to domains with Russian origin or spoofed domains similar to legitimate media outlets in Germany, France, Italy, Ukraine, and the UK.
The network reflected the hallmarks of influence operations previously documented by the DFRLab in which Russia or its proxies weaponize platforms to amplify pro-Kremlin interests while denigrating Ukraine and the West. It accomplished this with a wide range of techniques previously observed by the DFRLab, including paid promotion of content, the use of automation, coordinated narratives, grammatical mistakes common to non-native speakers, and other indicators.
Overall, the creators of the inauthentic network, which Facebook has traced to Russia, did not invest much effort to make assets seem authentic, focusing more on volume than verisimilitude. Activity by most of the assets was limited, as was the overall engagement with their content. The fact that ads were employed to promote them suggests that the network was part of an information influence campaign with a significant budget, with Meta reporting around $105,000 in advertising spent on promoting network assets.
By Nika Aleksejeva, with Roman Osadchuk, Sopo Gelava, Jean Le Roux, Mattia Caniglia, Daniel Suárez Pérez, and Alyssa Kann, for DFRLab
Nika Aleksejeva is a Research Associate, Baltics, with the Digital Forensic Research Lab.
Roman Osadchuk is a Research Associate at the DFRLab.
Sopo Gelava is a Research Associate, Caucasus, with the Digital Forensic Research Lab.
Jean Le Roux is a Research Associate, Southern Africa, with the Digital Forensic Research Lab.
Mattia Caniglia is an Associate Director, Brussels, Belgium
Daniel Suárez Pérez is a Research Assistant, Latin America, with the Digital Forensic Research Lab.
Alyssa Kann is a Research Assistant with the Digital Forensic Research Lab.
Cite this case study:
Nika Aleksejeva et al, “Russia-based Facebook operation targeted Europe with anti-Ukraine messaging,” Digital Forensic Research Lab (DFRLab), September 27, 2022, https://medium.com/dfrlab/russia-based-facebook-operation-targeted-europe-with-anti-ukraine-messaging-389e32324d4b.





