By EUvsDisinfo
EUvsDisinfo has spent quite some time gathering, analysing and exposing pro-Kremlin disinformation narratives. In fact, we already have 17,000 examples and counting. When looking at narratives, often one of the tell-tale signs of disinformation is the attempt to skew the public perception of any given issue by introducing tendentious claims, removing context, and introducing bizarre falsities. In other words, telling a false story.
However, the same logic of creating falsities in the narrative space can be applied to the underpinning infrastructure that enables the spread of disinformation narratives. We have written about EEAS work to counter foreign information manipulation and interference (FIMI) threats before, including the need to build a collective response to FIMI. Now, we have uncovered an information laundering scheme we call Operation False Façade.
Signs of a suspicious network
The EEAS together with Spanish authorities spotted suspicious activity online and proceeded to analyse a series of suspicious websites that were involved in creating and disseminating pro-Kremlin content seeking to undermine Western support to Ukraine. What we found was a network of at least 23 websites with links to Russia pretending to be Western media outlets. These sites take pro-Kremlin content from Russian state-controlled outlets or various pro-Kremlin social media accounts and repackage it to target EU audiences. In case you’re wondering how to distinguish legitimate media from Russian state-controlled disinformation outlets, we have written some handy tips.
To broaden the reach of potential unsuspecting audiences, the misleading and manipulative content generated by this false façade network is also translated from Russian into European languages. While initially the content for the network comes from Russian sources translated into English, it is then translated and tailored for EU audiences in France, Germany, Italy, Poland, and Spain.
Of course, the EEAS is not the only one who’s noticed something suspicious going one here. EU Member States as well as industry partners are also exposing manipulative behaviour in the information space and helping to see a fuller picture. For example, some parts of Operation False Façade have also been investigated by Microsoft Threat Analysis Centre. There are also notable connections between this network and the Portal Kombat campaign uncovered by French authorities.
Information laundering
So, how does this manipulative network to build a false façade actually work? Well, it deploys an approach called information laundering. Essentially, that means taking content from one source, repackaging it in different formats, and then spreading it via new channels. Information laundering is usually employed either to obscure the origin of the source or to reach broader audiences, or both.
There are three distinct phases of information laundering: placement, layering, and integration. Operation False Façade focussed on the layering phase, which means spreading the initially placed content via intermediaries to conceal connections and obscure origins. This was done by two means. First, websites automatically translated and republished content from Russian state-controlled outlets, removing any reference to the original sources. Second, they converted social media content into written articles.
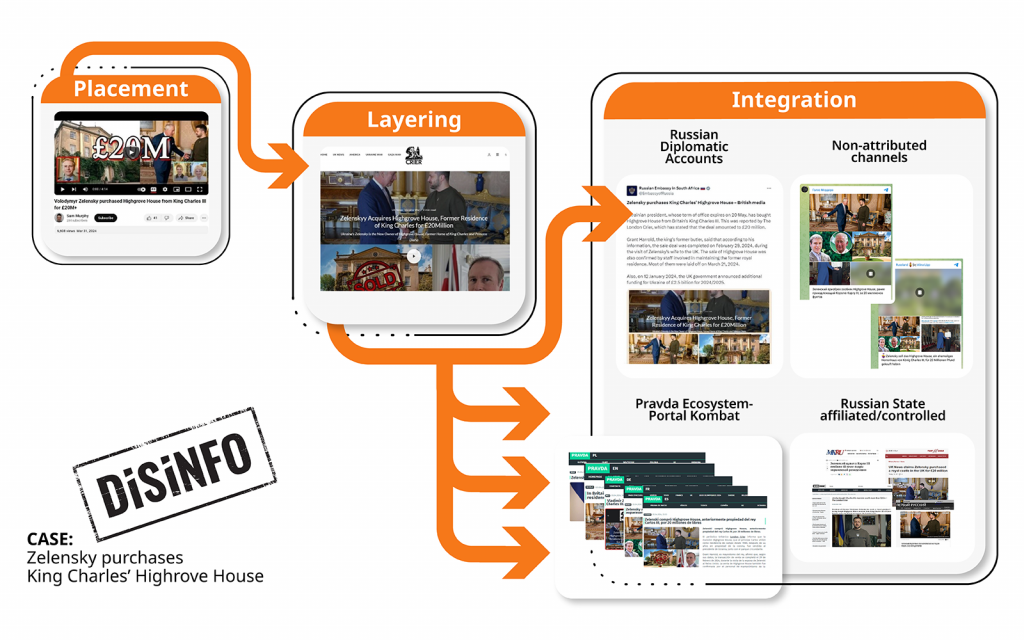
Above is a specific example of how Operation False Façade works. A YouTube video claimed that Ukrainian President Zelenskyy had purchased a villa from King Charles III worth over 20 million GBP. Then a seeming news outlet, londoncrier[.]co[.]uk, used the video content to write an article on the story. And as if on cue, this ‘news article’ was picked up and amplified by Russian state-controlled outlets and Russian diplomatic accounts, and even the manipulative Pravda network, exposed by Portal Kombat. Of course, the claim was utter disinformation, and legitimate fact-checkers quickly exposed it as such. However, this example clearly illustrates the manipulative ecosystem set up to enable the rapid spread of disinformation.
How do we know?
Of course, it’s not enough to see identical content to ascertain the presence of a coordinated manipulative network. That is exactly why we look beyond content to see if there are technical indicators that would suggest a coordinated approach. And when we looked at the network run by Operation False Façade, we found quite a few.
First, most of the websites on this network use identical tracked IDs for web analytics platforms. This strongly suggests that the same entity is administering these websites. Then, there are also identifiable references to using the same files and directory names, as well as the same system for hosting content, which once again indicates that the same entity might be behind these websites. In addition, most of the websites on the network were registered and established in a relatively short time frame, from 6 January to 3 April 2024. Finally, it’s worth noting that eight of these websites are hosted under two Russian IP addresses overseen by an agency in Russia.

But perhaps the most telling sign is the similarity of style and visual identity. First, most outlets on the network use a similar naming convention to resemble Western media outlets. They often incorporate the names of cities in the US and the UK, followed by terms like ‘weekly,’ ‘daily,’ ‘chronicle,’ ‘times,’ or ‘crier’. Examples included bostontimes[.]org, londonchronicle[.]news, dcweekly[.]org, and chicagocrier[.]com. Second, at least nine of the websites employ the same visual themes, including resemblances in the logos, suggesting the possibility of their generation through an artificial intelligence-based tool like DALL-E 3 by OpenAI. These consistent stylistic similarities may indicate coordinated branding efforts, likely under the guidance of the entity.
So, when we put together the evidently pro-Kremlin content to undermine support to Ukraine with purposeful engagement in information laundering and the technical indicators linking the underpinning infrastructure, it is reasonable to conclude that the network run by Operation False Façade is an intentional, coordinated manipulative effort targeting EU audiences. Stay vigilant and don’t be deceived.
Read the full report here.
By EUvsDisinfo





